This American Historical Review was unlike any other that I have read. The read itself was not difficult to get through but the amount of digital information that was linked to this particular historical review was a little over whelming. There was so much information to look at and there was what seemed to be an abundant amount of sources that was referenced to support the arguments that were being made.
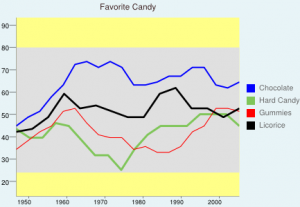
If I was going to to use this historical review to write a paper I would want to check the authenticity of the references to ensure that the information that was being provided was authentic and true. The section Methods was in my opinion, the most important section of this historical review that tied into what we are currently doing in this class. It was interesting to read about how the use of digital mapping with historical content was tied together to create all of the information that was in this website. The digital material that was provided by this historical review gave a great visual representation of the central argument that this review was making. I think that it was essential that this review have the section Methods to provide the readers with some knowledge of how to interpret the digital maps that were provided and how the historical information played a key part in making the maps.
Reading this historical review was a great experience and it really shed some light on the use of digital materials to drive home an argument.