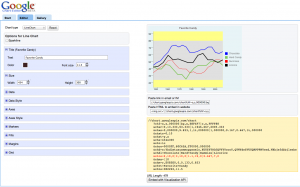
Putting together this map was a lot of fun. I had a couple of issues because I wasn’t using the proper application to create the map with layers. I was using the map application instead of Google Earth. After figuring out with application I needed to use to get this map put together the rest was pretty easy. Placing the map on top of the other map and making sure that everything aligned did present a bit of a challenge especially since some main terrain features had changed or they just might not have been drawn with the accuracy of using a satellite.
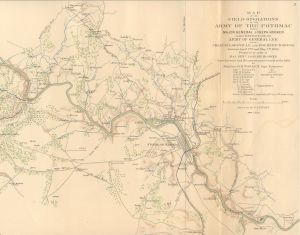
I found this old map from 1863 of Fredericksburg, Virginia. Once I had the layer on the map I quickly noticed that there were some terrain features that were different and some parts of the maps were not matching up with the satellite view from Google Earth. This exercise was fun and finding old maps of an area that I am familiar was very interesting.
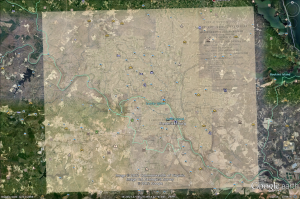
Here is the map that I created. Once the layer was inserted it was interesting to see that I could not keep the original ratio of the map while increasing the size of the map. It was a bit of a challenge at first trying to get the layer to a similar size of the area that the map was covering. After some pulling of the corners and rotating the layer a few hundred times I feel that I got the layer on top of Google Earth’s view as close as possible. The only feature that I would change when adjusting the layer is having the option to lock the ratio of the map that has been inserted until you get it to the size that you wanted, then you can push and pull the corners as you desire.